

WannaCry Ransomware: How it Started and Where it Stands Now

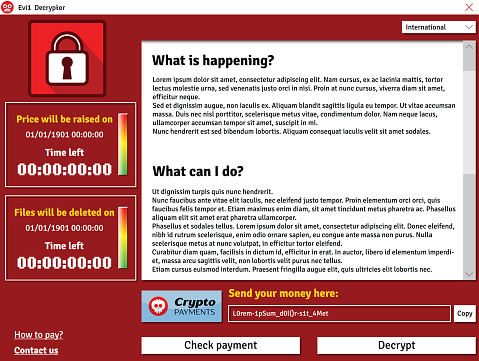
WannaCry is an infamous example of how dangerous ransomware can be in the modern world. Almost overnight, this cyber attack hit computers around the world and managed to infect 300,000 computers in more than 150 countries before going back to the benches for a break.
Ransomware is particularly dangerous because, unlike many types of malware, it has a particular purpose: It tries to extort money from victims by holding data hostage. In this case, WannaCry spread its way through unprotected Windows computers, locking away valuable files and changed desktop backgrounds into a set of commands to submit money to the hacker via bitcoins. Here’s how it played out.
How WannaCry was Born
WannaCry is an interesting version of ransomware because of the way that it spreads. Most ransomware starts with a relatively simple phishing email that encourages victims to click on the link and so download the malware. WannaCry, short for Wanna Decryptor, spreads itself through the Server Message Block protocol, which is used by Windows computers to share files. That makes it very easy for the malware to jump between different computers that are on the same Windows network (the actual mechanics of making that jump are still somewhat unclear). This makes the ransomware particularly dangerous for business and school computers that are regularly connected on large networks. It even managed to infect high-level government organizations in countries like the UK.
When inside a vulnerable computer, WannaCry chooses specific files types – files types generally known for their valuable data content – and creates an encrypted copy of them using AES and RSA encryption techniques, which makes it very difficult for anyone but the hacker to decrypt the files. The encrypted versions replace the old files, and the ransomware displays the extortion message.
How Security Experts Tackled the Ransomware
Actually, it was one security expert in particular that cracked the code to shut down WannaCry before it did, even more, damage: A 22-year old anonymous malware researcher who digs into these problems for a living took a close look at WannaCry and found a significant vulnerability.
Most ransomware has a simple test that it runs when it firsts attacks a computer. This involves sending out a request to a website that doesn’t exist in the real world. This request is designed to fail. Ransomware is often tested in secured simulated environments by security experts looking for a weakness, so it is usually programmed to avoid infected computers in such a simulated network. A simulation wouldn’t route this website request to the real Internet, so the check would pass, and the ransomware would know it was a trap.
The UK white hat hacker came up with a simple solution based on this reaction: He simply bought a real domain for about $10 with the exact same name as the nonsense website that the WannaCry ransomware was programmed to check for. Suddenly, whenever WannaCry checked for the site on any connected computer, it came up positive. The ransomware immediately started thinking that everything was a trap, and it shut down instantly.
Why WannaCry is Still a Problem
Despite the clever solution, WannaCry remains a problem. That’s because hackers can’t resist a successful piece of ransomware, and copycat versions of the attack have already begun. At least two versions have come up with workarounds to the kill switch, including choosing a different target website for the test.
These versions of WannaCry remain less dangerous than the first because 1)we know about them and 2)they were sloppy copies from amateurs, but this doesn’t mean a bigger, badder WannaCry 2.0 isn’t on its way.
The Lessons We Can Learn
Don’t stick with older operating systems! WannaCry was a big problem for two reasons. First, while Microsoft released a patch that would have prevented the issue back in March, far too few people – including organizations that should have known better – downloaded it. That’s why it’s usually a good idea to have automated update schedule enabled, or at least clear instructions after an important patch is released.
Second, don’t get stuck in the dark ages. It took Microsoft a lot longer to create updates for outdated systems like Windows XP, which proved the most vulnerable platform by far for WannaCry. Guess who still uses Windows XP? If you answered, “Governments and lazy businesses,” then you are absolutely right, and they were also the most common victims of WannaCry. It’s all right to wait for compatibility and stability checks, but upgrading to new versions of the OS is important as soon as it is possible.
For more ways to protect your New England business, contat Vertical IT. Feel free to ask us any specific questions by contacting us at info@verticalitcorp.com or (888) 505-8215.